- Se incorporó
- 1 Febrero 2007
- Mensajes
- 4.868
Estimados
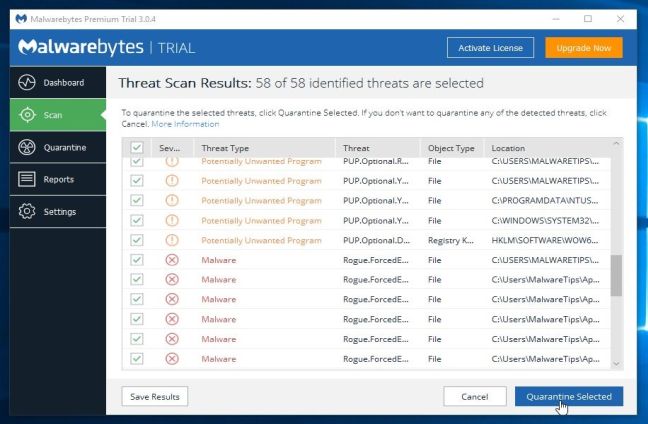
Me llego un equipo donde aparentemente todos los archivos esta corruptos. buceando por el sistema de archivos me encuentro con .txt llamado " HELP_DECRYPT"
al leerlo , tiene esto
Segun eso , los archivos tan encriptados y que seguramente pedira pago en una pagina rancia , alguien le ha pasado esta gracia jajaja
jajaja
Me llego un equipo donde aparentemente todos los archivos esta corruptos. buceando por el sistema de archivos me encuentro con .txt llamado " HELP_DECRYPT"
al leerlo , tiene esto
Código:
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048 using CryptoWall 3.0.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1.http://ayh2m57ruxjtwyd5.abctopayforwin.com/bN8UQ2
2.http://ayh2m57ruxjtwyd5.bcdthepaywayall.com/bN8UQ2
3.http://ayh2m57ruxjtwyd5.deballmoneypool.com/bN8UQ2
4.http://ayh2m57ruxjtwyd5.armnsoptionpay.com/bN8UQ2
If for some reasons the addresses are not available, follow these steps:
1.Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2.After a successful installation, run the browser and wait for initialization.
3.Type in the address bar: ayh2m57ruxjtwyd5.onion/bN8UQ2
4.Follow the instructions on the site.
IMPORTANT INFORMATION:
Your personal page: http://ayh2m57ruxjtwyd5.abctopayforwin.com/bN8UQ2
Your personal page (using TOR): ayh2m57ruxjtwyd5.onion/bN8UQ2
Your personal identification number (if you open the site (or TOR 's) directly): bN8UQ2Segun eso , los archivos tan encriptados y que seguramente pedira pago en una pagina rancia , alguien le ha pasado esta gracia
 jajaja
jajaja